Home
Resources
Webinars
DNS fragmentation attacks – the dangers of not validating DNSSEC.
ARE YOU INTERESTED IN LEARNING HOW YOU CAN PREVENT DNS FRAGMENTATION ATTACKS ON YOUR NETWORK?
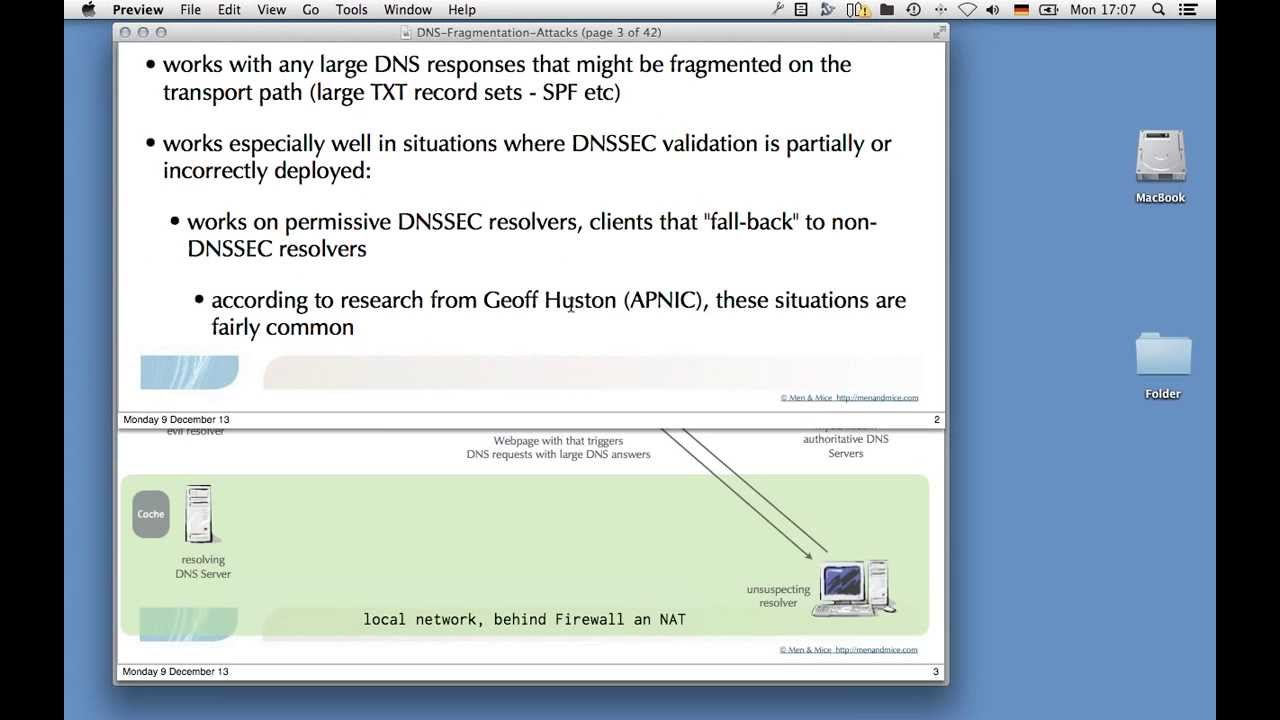
DNS, the Domain Name System, is an important and security-sensitive service to the Internet. DNS cache poisioning attacks can, and have been used, to redirect traffic within networks and are often the first step for larger attacks.
In August 2013, a new kind of DNS cache poisoning attack was made public to a broader audience by injecting wrong DNS data into caching DNS servers by manipulating fragmented DNS UDP responses.
At Men&Mice we are eager to share our knowledge so you can take action and prevent this from happening on your network.
One of our Professional Services team members, Mr. Strotmann goes over:
- why DNS fragmentation attacks work
- why DNS caching servers that do not do DNSSEC validation are especially vulnerable
- why DNSSEC signed zones can be used to launch this attack
- how IPv6 and/or DNSSEC validation can stop these attacks